[題目]
The purpose of this challenge is to demonstrate the MITRE Top 25 programming error: Integer Overflow or Wraparound.
You were able to guess the password but an account lockout mechanism has been enabled and the account is now locked out. However the lockout mechanism has a flaw.
You have the vulnerable code below. See if you can detect the issue and exploit it to login. Use the same password from the brute force challenge.
|
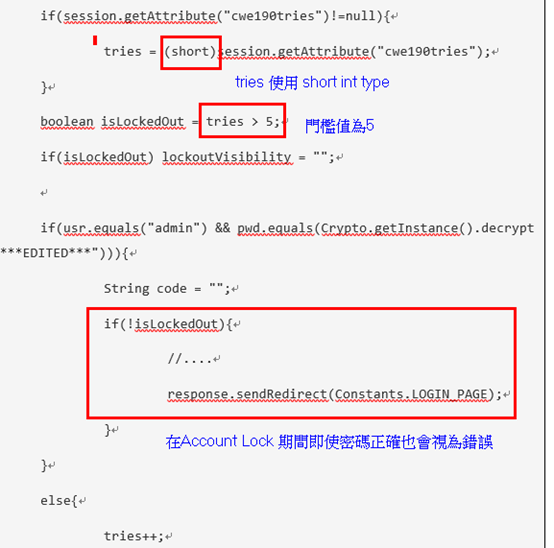
if(usr!=null && pwd!=null){ if(session.getAttribute("cwe190tries")!=null){ tries = (short)session.getAttribute("cwe190tries"); } boolean isLockedOut = tries > 5; if(isLockedOut) lockoutVisibility = "";
if(usr.equals("admin") && pwd.equals(Crypto.getInstance().decrypt("****EDITED***"))){ String code = ""; if(!isLockedOut){ //.... response.sendRedirect(Constants.LOGIN_PAGE); } } else{ tries++; alertVisibility=""; }
session.setAttribute("cwe190tries",tries); } |
[題目說明]
這一題是要我們根據以上的JSP Java Code 找出漏洞可以讓我們繞過登入錯誤限制次數的rule用猜測密碼攻擊方式。
[弱點提示]
The software performs a calculation that can produce an integer overflow or wraparound, when the logic assumes that the resulting value will always be larger than the original value. This can introduce other weaknesses when the calculation is used for resource management or execution control.
From MITRE CWE190
利用整數溢位的方法可以讓hacker繞過密碼錯誤輸入次數限制的rule進行密碼猜測攻擊,整數溢位的原理如下圖所示:
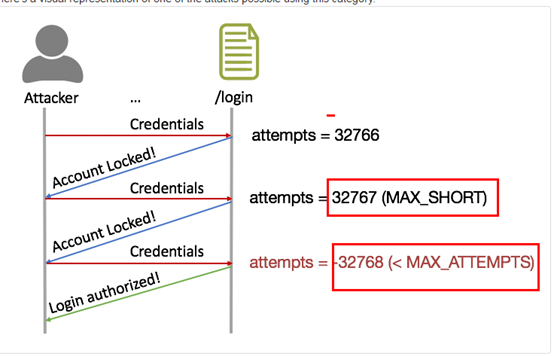
由於程式使用 short int 作為retry 次數的變數型態,當retry > threshold(正整數) 時雖然會觸動限制輸入錯誤密碼機制,但是由於short int 變數最大值為 32767 ,因此超出該值就會產生整數溢位,short int 變數將變成負數-32768,此時retry必然小於原本是正數的threshold,輸入密碼次數限制功能便被成功繞過,hacker此時便可以隨意進行密碼猜測攻擊,直到輸入正確密碼為止。
[解答]
- 進入網頁: https://abc.xxx.elasticbeanstalk.com/cwe190.jsp
- 隨意輸入多次密碼直到底下框框秀出Account locked out! There were -32768 tries.’’ 為止,此時便可以進行password guessing attacks: (注意: 在限制輸入密碼次數期間無論密碼正確與否都會導致密碼錯誤的結果,這也是為何要繞過該限制的原因。)
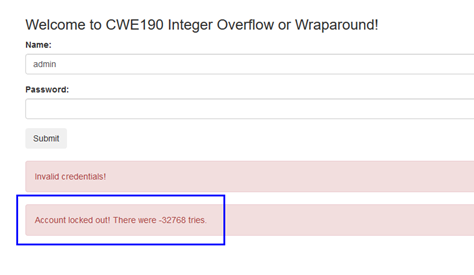
- 此時可以進行至少32768次以上的密碼猜測,若知道密碼直接輸入正確密碼(Iloveyou)即完成破解任務。
[安全原理]
該弱點被利用的關鍵在於hacker透過程式碼得知應用程式使用short int 變數來儲存retry 門檻值 5 ,雖然在retry 超過5次後就會啟動帳號鎖定機制,但因為retry仍會繼續累加變數值,所以當變數溢出32767便會變成負數-32768,hacker變成功繞過account lock ,此時只要繼續猜測到輸入正確密碼便可登入,這表示即使用retry限制來鎖定accout 仍會有安全風險,所以可以加上如capcha等機制來防範漏洞。
2019年2月21日星期四



 留言列表
留言列表

