[題目]
The purpose of this challenge is to demonstrate the MITRE Top 25 programming flaw: "Cross-Site Request Forgery (CSRF)".
About the Challenge
Just like in the challenge before you have to exploit the social networking feature where users can see each others profiles.
Use CSRF to cause any user that sees your profile to change their Display Name to Banjo
PS: The developers have introduced a feature to filter out tags and prevent the XSS seen in the previous challenge. You will have to figure out how to send the request to update other users profiles without using HTML markup.
[題目說明]
這一題是要我們CSRF的攻擊手法讓一個可以互相瀏覽彼此profile的網站內的user在load進網頁的時候,因為也要load進你的profile,然而你的profile藏有特殊http request,所以改掉了user的profile的display name。
[弱點提示]
The web application does not, or can not, sufficiently verify whether a well-formed, valid, consistent request was intentionally provided by the user who submitted the request.
From MITRE CWE352
CSRF是一種在user borwser端的攻擊,跟一般針對Server端的攻擊手法不一樣,其原理大致是利用user登入某一需要authentication 的銀行網頁之後,由於browser此時會存有銀行帳號密碼在cookie中,所以若hacker可以確定使用者已通過authentication且未離開網頁,則只要想辦法讓使用者在某格地方接收到一個http request 利用browser cookie的credential 來進行某些銀行網站內容更改的動作(如轉移使用者銀行存款),就達成CSRF的目的。
CSRF並不容易理解,故題目舉了一個例子給大家參照:
A Bit About CSRF
CSRF and XSS are related. They are both part of a category of attacks known as Client Side attacks. They are called this way because they occur in the browser and usually have the target the user of the application rather than the server.
If an application only relies on cookies to validate the authentication of a request, it allows CSRF.

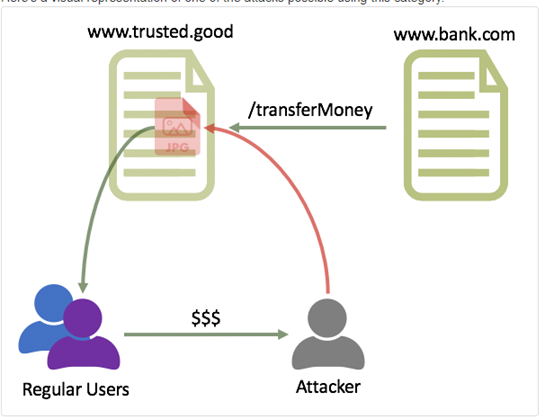
Consider the following attack scenario.
- When your browser loads the discussion board, it will automatically send the request that was stored in the attacker's avatar using the active cookies from the bank tab
- You are browsing the Internet, in one tab you have your banking site while in another you have your favorite discussion board.
- One of the users of the board has replaced their avatar with an HTTP request to your bank transferring $100 to an overseas account.
[解答]
- 進入網頁: https://abc.xxx.elasticbeanstalk.com/cwe352.jsp
- 用demo身分登入網頁
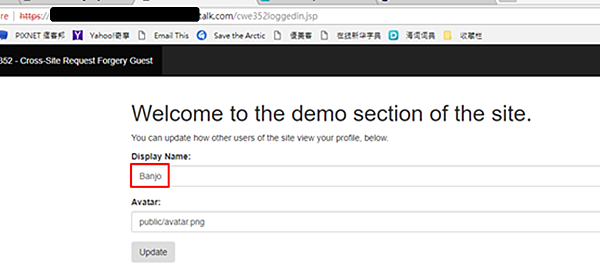
- 此時hacker進入到一個可上傳檔案的頁面,在Display Name輸入Banjo然後按Update 鈕。

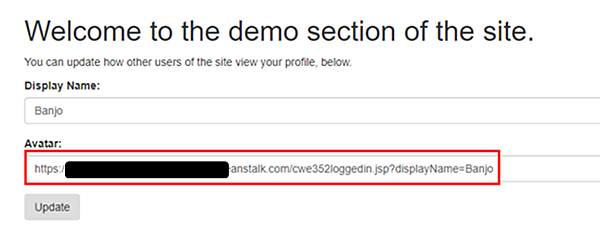
- Copy URL到 Banjo
![]()
- 把URL貼到頭像上傳欄位再按下Update鈕然後過關。

[安全原理]
之所以把該http request url貼到頭像欄然後上傳就過關的原因是: 該url視做把user profile名稱改名Banjo的動作,而在該網頁中任何人都必須Load進別人的profile,且可以進到該網頁的必定是合法使用者,所以當user load到你的這個http request 頭像時,便會執行更名指令,自然把user的profile display name改成Banjo了。
2019年2月22日星期五



 留言列表
留言列表

