[題目]
The purpose of this challenge is to demonstrate the MITRE Top 25 programming flaw: 'Incorrect Authorization'.
The developer of the vulnerable application has finally implemented authorization for the admin page. Both admin and user pages are handled by the same JSP. You have the vulnerable code below. See if you can spot the programming error.
if(session.getAttribute("ch3loggedin")==null || !(boolean)session.getAttribute("ch863loggedin")){
response.sendRedirect("ch863.jsp?loggedin=false");
}
else{
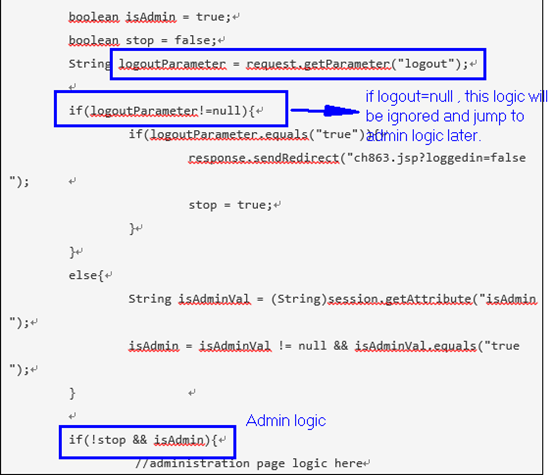
boolean isAdmin = true;
boolean stop = false;
String logoutParameter = request.getParameter("logout");
if(logoutParameter!=null){
if(logoutParameter.equals("true")){
response.sendRedirect("ch863.jsp?loggedin=false");
stop = true;
}
}
else{
String isAdminVal = (String)session.getAttribute("isAdmin");
isAdmin = isAdminVal != null && isAdminVal.equals("true");
}
if(!stop && isAdmin){
//administration page logic here
//...
}
}
|
[題目說明]
這一題純粹就是程式沒寫好有漏洞,所以hacker有辦法在url中動手腳繞過程式機制存取Admin空間,你所要做的就是在url中動手腳。
[弱點提示]
The software performs an authorization check when an actor attempts to access a resource or perform an action, but it does not correctly perform the check. This allows attackers to bypass intended access restrictions.
From MITRE CWE863
[解答]
- 進入網頁: https://abc.xxx.elasticbeanstalk.com/cwe863.jsp
- 登入guest account : demo / demo1234
- 進入user頁面後,將url 加上 ?loggout=null 再送出,就可以獲取admin權限。 url = https://abc.xxx.elasticbeanstalk.com/cwe863loggedin.jsp?logout=null
[安全原理]
從程式面看,logout parameter值只要是null就可以跳過authorization check直接進入admin logic,這是把user與admin的logout logic寫在一起造成的問題。
2019年2月23日星期六



 留言列表
留言列表

