[題目]
The purpose of this challenge is to demonstrate the Use of Externally-Controlled Format String, MITRE Top 25 vulnerability.
The developers of the master password app have implemented the safe function fgets so buffer overflow is no longer possible. However you may be able to obtain data from the memory. You don't need to get the password, just some memory values are enough to pass the challenge.
|
#include <stdio.h> #include <string.h>
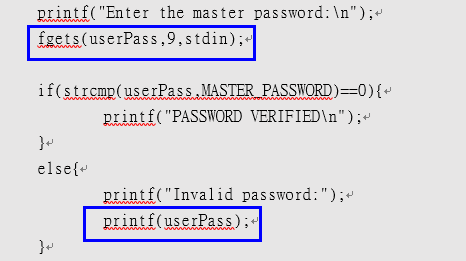
int main(){ char MASTER_PASSWORD[9]="***EDITED***"; char userPass[9]; int x=2; printf("Enter the master password:\n"); fgets(userPass,9,stdin);
if(strcmp(userPass,MASTER_PASSWORD)==0){ printf("PASSWORD VERIFIED\n"); } else{ printf("Invalid password:"); printf(userPass); } return 0; } |
[題目說明]
這一題是要我們利用C語言的format string使用方式來獲取變數的memory資訊。
[弱點提示]
The software uses a function that accepts a format string as an argument, but the format string originates from an external source.
From MITRE CWE134
該題中developers已經用fgets() function來避免發生buffer overflow漏洞,但是hacker仍可透過format string的輸入方式讓程式洩漏特定變數的記憶體位置,這是因為fgets()並未阻擋任何來自於使用者的input,而使用者input包含format string 格式的字串。
[解答]
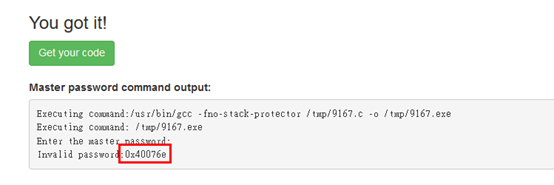
- 進入網頁: https://abc.xxx.elasticbeanstalk.com/cwe134.jsp
- 輸入 %p 後按Submit即可看到UserPass變數的記憶體位置。

[安全原理]
關鍵就在於程式碼fgets()的輸入來源是stdin,在未給予輸入值檢查的情況下,我們可以輸入”%p”然後透過fgets() 餵給userPass,而%p將會列出變數userPass的memory address,由於密碼是錯誤的,所以printf(userPass)便會是printf(%p),把userPass的memory address print 出來。

2019年2月26日星期二



 留言列表
留言列表

