
今天來介紹一篇顏值好像不措的hacker news: CyberSecurity Framework,主要是講述企業需要一套網路安全相關的策略框架來強化企業(Enterprise)資訊安全的作業環境。
該文前面講了一些比較不重要的話,直接從重點內文切入:
What is a Cybersecurity Framework?
什麼是Cybersecurity Framework呢?以下是它的定義:
Cybersecurity framework is a predefined set of policies and procedures that are defined by leading cybersecurity organizations to enhance cybersecurity strategies within an enterprise environment
簡單說就是一套由資安領導大廠定義的一連串程序與政策來加強企業環境的電腦安全策略。
These frameworks are, at times(有時), designed targeting a specific industry and are built to reduce the unknown vulnerabilities and misconfigurations existing within an enterprise network.
這個電腦安全框架也可以說是重視於網路安全,重點在減少資安弱點與錯誤的環境配置造成的安全風險。
Cybersecurity Framework Strategies
這裡講述了資安框架的組成元素,這些元素可幫助實現企業的資安防護策略。其中包括:Identify(識別)、Protect(保護)、Detect(偵測)、Respond(回報)、Recover(發現)。
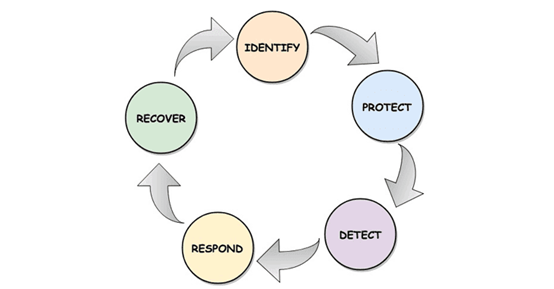
- Identity : 幫助企業辨別企業內部可被觸碰到的電腦進入點,包括IT資產、資源、資訊等等。
This function helps the organization identify the existing cyber touch points within a business environment. Those could be IT assets, resources, information, and more. - Protect : 對於企業內部與Business內容相關的存取控制以及資料保護採取主動防護策略。
This one takes care of corporate access control, data security, and maintenance to take care of cybersecurity in and around the business environment. Most likely, it is a proactive phase of enterprise cybersecurity. - Detect : 企業必須藉由log分析以及針對網路和資訊裝置進行入侵偵測以找出任何潛在漏洞(breach)。該階段包含了整個安全資訊與事件管理作業。
This function is where an organization will identify any potential breaches by monitoring the logs and taking care of intrusion detection procedures at the network and device level. Security information and event management are all covered under this procedure. - Respond : 在發現潛在的漏洞之後,必須進行漏洞回報與修復,減輕漏洞危害以及製定改善快速回報漏洞計劃都是這一階段的任務。
Once the breach is detected organizations need to take care of the respond procedure—understanding the breach, fixing the vulnerability, and proceeding with the recovery. The mitigation, response planning, and improvements will be handled at this stage. - Recover : 製定系統復原計劃,以因應災難發生時必須的系統回復和備份計劃。
Recover planning procedures, like disaster recovery system and backup plans, will be handled in this stage of the cybersecurity framework strategy.
Types of Cybersecurity Frameworks
這裡列出了一些比較多人知道的資安框架標準給大家參考:
- ISO 27001/27002 : 仿造製造業用的ISO9000製作的資安標準協議,ISO27001 定義了資安需求; ISO27002 則定義了資安實作細節。
Considered as an equivalent to ISO 9000 standards for manufacturing, helps organizations define and measure their quality of cybersecurity existing within their environment.
ISO2700 defines an overview, while ISO27001 takes care of the requirements, and ISO27002 takes care of the implementation procedures.
- CIS Security Control: CIS是Center for Internet Security的縮寫,其定義了20個 關鍵安全控件(Critical Security Control)讓企業實作,企業要建立安全的網路安全環境,至少必須建立10項CIS的安全控件,當然最好是能20項全部建立。
CIS has defined three sets of critical security controls—they are basic, foundational, and organizational—counting 20 controls altogether. They address various security controls that should be existing inside an enterprise environment.
- NIST Framework: NIST 是The US National Institute of Standards and Technology 的縮寫,可想而知這是針對政府部門的安全標準,但也可應用於其他工業上。
- PCI DSS: PCI DSS 是 Payment Card Industry Data Security Standard 的縮寫,基本上就是保帳信用卡/現金卡進行線上交易的安全規範。
以上所有標準規範都有制式文件可供參閱實作。
All these frameworks are built and documented to make sure enterprises are practicing the industry standards and keeping their security clean and safe.
Implementing cybersecurity frameworks
最後一段講述實作資安框架的建議步驟,基本上只列出以備考,不另翻譯,真要簡要地說明,就是在企業決定要實作上述的任何一種CyberSecurity Framework時,應該先評估分析企業內達成的安全控件有哪些,還缺少的要如何與Framework整合加強,然後與主管溝通是必要的事。
- Businesses first need to test and identify the current security posture inside their environment
- Analyze the existing projects, the process involved in these projects and the resources involved with it
- Understand the cybersecurity framework by reading through the documents
- Distinguish what security controls exist and doesn't exist within the enterprise network
- Communicate where the security layers are lagging and define a plan to establish the same
- Implement the same in a defined time-frame to keep things on track and time
- Highlight controls that outperform the controls defined by the framework
- Discuss the entire plan with the key players, including stakeholders, and proceed with the implementation
- Audit the progress of implementation continuously
- Generate reports and conduct meetings to measure the challenges
- Document the entire process for audits and other benefits
[Reference]
2019年8月28日星期三



 留言列表
留言列表

