[題目]
The purpose of this challenge is to demonstrate the MITRE Top 25 programming flaw: 'Use of a Broken or Risky Cryptographic Algorithm'.
This is the same vulnerable application from the previous challenge. The developers are now hashing the user password but is it the right algorithm? They still haven't fixed the missing authorization issue by the way.
Did you know that the site CrackStation.net maintains a list of known hashes for numbers and dictionary words, also known as a 'Rainbow Table'?
Obtain the password for user and login to solve the challenge. See if you can spot the problem in the code below.
|
<!--contents of administration page cwe327admin.jsp--> ... byte [] hash = Crypto.getInstance().getHash(tmpPwd,"SHA-1"); tmpPwd = Util.bytesToHex(hash); ... |
[題目說明]
這一題是要我們根據以上的JSP Java Code 找出漏洞可以讓我們知道某特定使用者密碼然後直接駭入該使用者帳號。
[弱點提示]
Periodically ensure that the cryptography has not become obsolete(過時的). Some older algorithms, once thought to require a billion years of computing time, can now be broken in days or hours. This includes MD4, MD5, SHA1, DES, and other algorithms that were once regarded as strong.
From MITRE CWE327
如果使用者資料庫之中並未把密碼適當地加密儲存那很容易被Hacker透過某種管道取得使用者密碼,因此無論何時都應該將使用者密碼做加密,同時加密用的演算法必須是夠安全難以破解的(MD4, MD5, SHA1, DES 是不安全的),且盡量不要呈現使用者帳密資訊在頁面上。
[解答]
- 進入網頁: https://abc.xxx.elasticbeanstalk.com/cwe327
- 用demo與demo1234 帳密登入一般使用者頁面,該頁面是無法顯示使用者帳密資訊的。
- 只要把 URL 改成如下破解Admin管理密碼管理頁面(這是承襲Dojo 3的破解技巧): https://abc.xxx.elasticbeanstalk.com/cwe327admin.jsp?cwe327loggedin=1111 在該頁面取得user的tempory password hash:

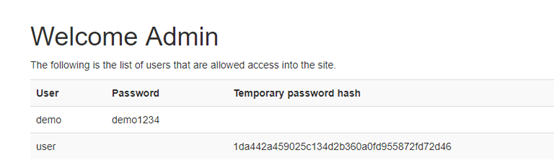
- 但因為取得的密碼是SHA-1 hash過的,所以必須將密碼用線上工具還原,打開CrackStation.net頁面貼上hash code即可還原sha-1密碼。

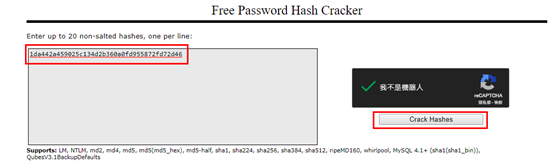
- 按下Crack Hashes即可得明碼。
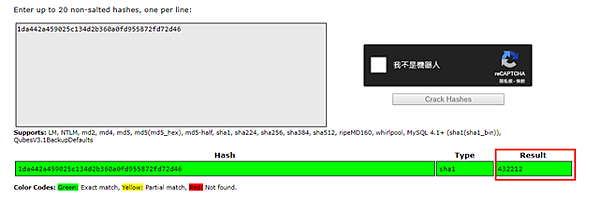


- 按Logout鈕登出後用user 帳密登入頁面即可破解頁。
[安全原理]
該弱點被利用的關鍵在於hacker登入頁面後用上一題missing authorization漏洞成功看到cwe327admin.jsp網頁內容,該內容是使用者帳密列表,因此hacker很輕鬆地拿到user 的密碼,雖然該密碼經過SHA-1加密,但是SHA-1是不安全的演算法,很容易透過工具破解,如此等同於hacker已經拿到目標帳號與密碼,達成竊取帳號目的。
2019年2月20日星期三



 留言列表
留言列表

