[題目]
The purpose of this challenge is to demonstrate the MITRE Top 25 programming flaw: 'URL Redirection to Untrusted Site ('Open Redirect')'.
Open Redirect is a very dangerous vulnerability. Attackers will manipulate legitimate urls to do their bidding. First the attacker would make the url very long would some 'bogus' parameters which will be ignored.
Example:
The victim will examine the first portion of the url and then give up. They will trust the URL since it's a valid url to 'www.mybank.com' and navigate to it.
About the vulnerable application
The developer of the vulnerable application has received a requirement to automatically redirect the users back to the page they were on, before the session expired and they were logged out.
Here's how the feature was implemented:
- When the session expires the authentication filter obtains the current relative resource path.
- The authentication filter then takes the url of the login page and appends the current relative resource path to it as a redirect parameter.
- The authentication filter then redirects to the newly constructed login page URL.
- The login page validates the user credentials and then obtains the value of the redirect parameter and redirects to it, without doing any verification of the URL.
Your task is to construct a URL that you can then send in a phishing e-mail to trick the admin into navigating to a malicious page and providing their credentials.
You must redirect the user to: http://evil.bad Simply navigate to the evil url that you end up making to complete the challenge.
You have some of the application code below. See if you can spot the issue..
<!--Code of the login form JSP-->
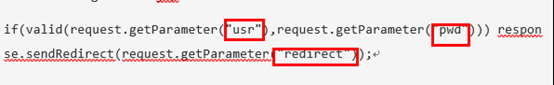
<form action="cwe601.jsp?redirect=<%=request.getParameter(redirect)%>>" autocomplete="off" method="POST"> <div class="form-group"> <label for="usr">Name:</label> <input type="text" class="form-control" id="usr" name="usr" value="admin"> </div> <!-- disables autocomplete --><input type="text" style="display:none"> <div class="form-group"> <label for="pwd">Password:</label> <input type="password" class="form-control" id="pwd" name="pwd"> } |
//code of login form jsp
if(valid(request.getParameter("usr"),request.getParameter("pwd"))) response.sendRedirect(request.getParameter("redirect"));
|
[題目說明]
這一題是要我們設計一個釣魚網址給使用者,該網址是利用web application提供的redirect導轉參數讓使用者按下釣魚網址之後會被導轉到我們所期望的頁面,且該頁面將竊取使用者在某一正常網站的帳密資訊。
[弱點提示]
A web application accepts a user-controlled input that specifies a link to an external site, and uses that link in a Redirect. This simplifies phishing attacks.
From MITRE CWE601
一個 Web Application 程式提供一個url可以接受使用者指定redirect的參數將該頁面導到外部網站去,如此該url將很容易被hacker用來作為釣魚網址騙取使用者帳密資訊。
[解答]
- 進入網頁: https://abc.xxx.elasticbeanstalk.com/cwe601.jsp
- 此時可以看到該頁面後面被加上了一個redirect參數。

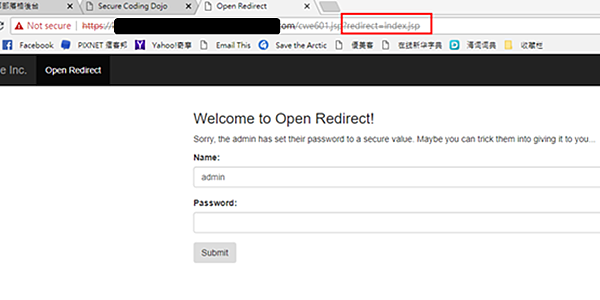
- 修改redirect 參數使他導轉到http://evil.bad及破解該任務。
[安全原理]
Redirect url是一個很危險的漏洞,因為通常使用者登入一個網頁後,hacker可以假裝送一個該web application with redirect 的url給該使用者騙取該使用者點擊連結,實際上被redirect hacker所期望的網頁,此時若redirect url若帶有帳密資訊的參數,hacker便可以輕鬆竊取使用者帳密。
2019年2月21日星期四



 留言列表
留言列表

