[題目]
The purpose of this challenge is to demonstrate the MITRE Top 25 programming flaw: "Unrestricted Upload of File with Dangerous Type".
To prevent the Cross-Site Request forgery demonstrated in the previous challenge, as well as the inclusion of files from untrusted domains, the developers are now only allowing users to upload avatars.
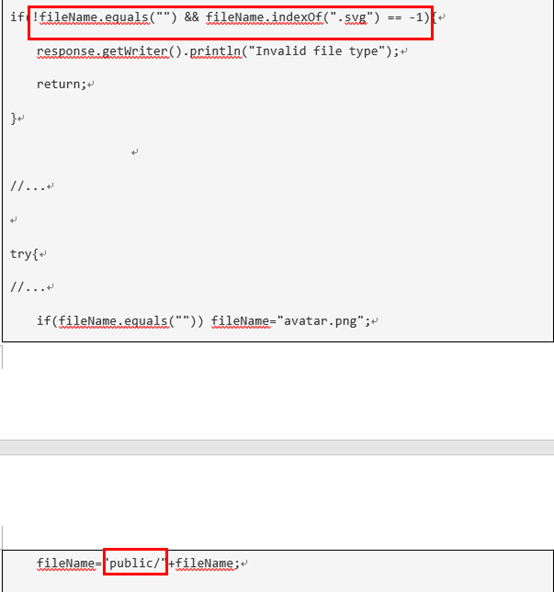
They are restricting the file types to SVG as shown in the code below. They are then saving the files on the system and loading them into the page via <img> references. Do you see any problem with that? Upload a file that could be used to execute code if it got uploaded to the Web directory of a Java web application. Like in this case the WebContent/public/ directory.
Tip: You need to upload some "server pages".
Part avatarPart = request.getPart("avatar");
final String fileName = getFileName(avatarPart); if(!fileName.equals("") && fileName.indexOf(".svg") == -1){ response.getWriter().println("Invalid file type"); return; }
//...
try{ //... if(fileName.equals("")) fileName="avatar.png"; fileName="public/"+fileName; //... if(avatarPart!=null) avatarData = Util.getStringFromInputStream(avatarPart.getInputStream()); request.getSession().setAttribute("cwe434avatarData",avatarData); try(PrintWriter out = new PrintWriter(fileName)){ //note we're not really doing this :) it's a simulation out.println(avatarData); } } catch(Exception ex){ response.getWriter().println(ex.getMessage()); } |
[題目說明]
這一題是網頁程式雖然用強迫使用者只能用選取檔案的方式上傳檔案以防止CSRF攻擊,但卻不限制不適當的檔案類型並把他放在可自動執行程式的資料夾目錄中,導致我們可以選擇危險的檔案,如JSP的網頁程式檔上傳,如此意味著hacker可以上傳惡意程式檔到Server中並自動執行。
[弱點提示]
The software allows the attacker to upload or transfer files of dangerous types that can be automatically processed within the product's environment.
From MITRE CWE434
Web Application僅限制使用者必須上傳檔名含有”.svg”的檔案到application中的有程式執行權限的目錄(Java的根執行目錄是/WebContent/public,可執行程式檔為.jsp),因此只要hacker上傳一個含有’.svg’檔名的jsp檔案就達成目的了。
[解答]
- 進入網頁: https://abc.xxx.elasticbeanstalk.com/cwe434.jsp
- Login with demo/demo1234.
- 在本機建立一個jsp檔案,檔名須包含: .svg , ex: example.svg.jsp
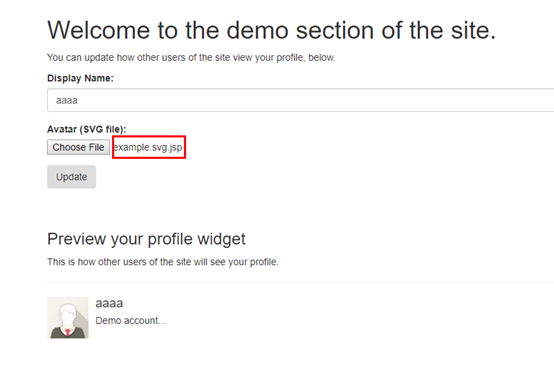
- Choose file ‘example.svg.jsp’ and then submit. Mission Completed!
[安全原理]
從程式碼看,該程式碼只限制使用者檔名必須有.svg的字眼,因此使用者依然可以上傳諸如 XXX.svg.jsp 檔名的檔案,同時預設該檔案會被放到有程式自動執行權限的public( java) folder底下,造成hacker可以植入惡意程式碼的風險。

2019年2月22日星期五



 留言列表
留言列表

