[題目]
The purpose of this challenge is to demonstrate several memory management issues specific to C/C++ applications. It specifically demonstrates the following two CWEs.
You found a page which is asking for a master password. It seems to be compiling and executing a C++ program under the covers. Bypass the simple hard-coded authentication below to solve the challenge.
Tip: To send \0 (a null byte) in a url use %00.
Also here is the master password program code. See if you can spot the problems.
#include <stdio.h>
#include <string.h>
int main(){
char MASTER_PASSWORD[9]="**REMOVED**";
char userPass[9];
printf("Enter the master password:\n");
gets(userPass);
if(strcmp(userPass,MASTER_PASSWORD)==0){
printf("PASSWORD VERIFIED\n");
}
else{
printf("Invalid password!\n");
}
return 0;
}
|
[題目說明]
這一題是要我們利用C語言的buffer overflow漏洞在密碼欄位輸入特定字元數之後讓原先密碼值被覆蓋,然後用strcmp只會比對到’\0’符號的方式讓密碼通過。
[弱點提示]
Buffer Copy without Checking Size of Input ('Classic Buffer Overflow')
The program copies an input buffer to an output buffer without verifying that the size of the input buffer is less than the size of the output buffer, leading to a buffer overflow.
From MITRE CWE120
簡易來說,變數都佔有一定的空間,當連續宣告兩個變數,他們應該通常是比鄰而居的,就好像兩個人住在隔壁一樣,這時候想像兩個人的房子是上下相疊的,如果第一人家淹水淹滿整間房子,溢出的水就會往下一間房子淹,這就是buffer overflow的原理,這一題就是要我們用字元數淹沒原本的密碼並且利用Strcmp函數的特性讓他比對到\0即停止來破解密碼,想了解更多原理,可以參考題目給的補充說明如下:
A Bit About Memory Flaws
Buffer Overflow types of attacks are extremely powerful and highly prized and seeked by cyber-criminals as well as intelligence agencies. Memory vulnerabilities account for many of the 0-days disclosed in web browsers and commonly used software such as Adobe Reader or Flash Player.
The reason they are so powerful is because they allow the attacker to execute arbitrary commands on the affected software. If that software happens to run with elevated privileges that is even better for the attacker, however 0-days are often chained together to give the attacker full system access.
Here is how memory flaws allow arbitrary code execution.
Imagine the program uses two variables a and b. The contents and length of variable b are controlled by the user. The variables are stored in the memory as seen in the simplistic example below. Each buffer may be reserved 16 bytes in a real program.

If the user enters the string AAAAA the following will happen.

The value of b will be AAAAAi! while the value of a will become Ai!. If the program outputs the value of b then the attacker will be able to know tke value of a which is known as a memory leak.
If the user enters a sufficiently long value they will hit the instruction area and be able to execute code.


.
[解答]
- 進入網頁: https://abc.xxx.elasticbeanstalk.com/cwe120.jsp
- 輸入 aaa嘗試登入,這一不會登入失敗是正常的。
- 獲取URL並把URL改成如下: https://abc.xxx.elasticbeanstalk.com/cwe120.jsp?pwd=%00aaaaaaaaaaaaaaa%00

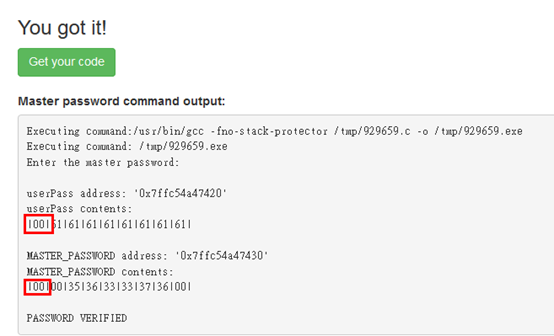
[安全原理]
為何輸入%00aaaaaaaaaaaaaaa%00就可以比對密碼成功呢?首先,先注意到userPass address = 0x7ffc54a47420;而MASTER_PASSWORD address = 0x7ffc54a47430, 由於address是16進制表示,所以兩個變數實際上差距16個bytes。
所以當userpass 變數的輸入字元超出16 位就會覆蓋掉MASTER_PASSWORD變數的值,而Strcmp只要比對到’\0’就會停止比對,所以我們讓第一個address 字元跟掉到MASTER_PASSWORD的第一個字元都是’\0’,這樣就可以比對通過而破解密碼驗證了。
2019年2月26日星期二



 留言列表
留言列表

